Farewell to Windows Server 20H2 and the Semi-Annual Channel. The copy highlights the importance and value of the deal BIGGEST SALE OF THE YEAR.

Get Private Online With Stop The Fomo Vpn Coupon Code Cyber Security Internet Speed Coding
Windows Network File System flaw results in arbitrary code execution as SYSTEM.

. It has become the center of gravity for almost every cryptocurrency news and projects. Find out how to join the future of cloud distribution. A graduate in the field of Cyber Security she has deep-rooted interests in modern technology naturally drawing her toward the expansive world of crypto and NFTs.
Perfect Day at CocoCay Bahamas and Orlando Florida. Bentuk praktis yang biasa dilakukan oleh penyedia layanan internet dalam memasarkan produk melalui konsep FOMO adalah menawarkan harga murah dengan ketersediaan dan waktu yang terbatas. Bitcoinist is a Bitcoin news portal providing breaking news guides price and analysis about decentralized digital money and blockchain technology.
Identity-based cyberattacks including credential theft credential abuse and long-term access key theft accounted for 56 of all incidents in Q2 of 2022 and Microsoft 365 remained the prime target for SaaS attacks according to Expels Quarterly Threat Report. Mereka pun kerap menggunakan diksi seperti jangan ketinggalan promonya awas rugi jika tidak menggunakan produk kami dan sebagainya. Programs Practices.
Profiting With 2 Benefits 3. Even cybersecurity professionals cant keep up. As of this year it has over 1000 cyber security specialists across 56 field offices.
Best TPM 20 Modules for Windows 11 in 2022. Could be implemented as a multi-step popup with a code reveal. Microsofts latest security patch troubles Windows 11 users.
The people that make us tick. Everything youll ever need is right here ready and waiting. Prime Day Deals.
In yesterdays PSA the FBI. By texting to 219 327-5005 you are agreeing to receive periodic text messages from Committee to Elect Jennifer-Ruth Green. By Jim Masters Aug 9 2022.
Project Serum market data. Its popularity is triggered by its encryption and security features. The contrasting CTA is a cant-miss.
MAXUSDT TRX is The Best Platform for Cloud Mining in Terms of Liquidity Security and Innovation YOLOREKT dApp is LIVE now. Dont suffer from FOMO. The FOMO win-back email example.
These episodes are a sampling of the weeks financial news and the impact on your personal finances. 500-10000 Rewards Profit Sharing To Recruit Skilled Traders Bexplus Announcing 5000 Rewards For New Users. Discover more about the Gamified-Social Price Prediction Platform We Want You.
He joined Juniper in 2016 and is the security subject matter expert for the corporate marketing team. Latest Webinar now available. Its simple really.
Laurence Pitt is Global Security Strategy Director at Juniper Networks. The Black FridayCyber Monday promotion makes the popup time-sensitive. Amazons new reality show Ring Nation featuring footage from its Ring home security cameras is the companys latest effort to normalize its surveillance network Amazons newest effort to normalize its surveillance network will feature footage from Ring surveillance cameras and commentary from comedian Wanda Sykes.
The 4 Night Bahamas. The final check-in win-back email template. The primary purpose of a marketing deck is to persuade your target audience about the value of your product service or business idea.
Stability is something that has been missing from. ZeroHedge - On a long enough timeline the survival rate for everyone drops to zero. Cyber Monday Laptop Deals.
Guidelines for an effective win-back email campaign. He has over twenty years of cyber security experience having started out in systems design and moved through product management in areas from endpoint security to managed. The just checking in win-back email example.
What are marketing decks for. Best Amazon Prime Day. What could be optimized or AB tested.
For individuals and teams. The irony is that never in the history of cyber. Microsoft tests CD ripping for Media Player in Windows 11.
There are a lot of headlines out there but we distill it down. Invicti Web Application Security Scanner - the only solution that delivers automatic verification of vulnerabilities with Proof-Based Scanning. Message and data rates may apply.
Cyber Monday Monitor Deals. Expel is a Top 250 MSSP and Top 40 managed detection and. Crypto telegram channels have emerged as the number one destination for news gossip FUD FOMO charts bots and project updates related to the world of cryptocurrencies.
Fortune 100 enterprises and cutting edge. Search for ticker symbols for Stocks Mutual Funds ETFs Indices and Futures on Yahoo. Create a great subject line.
The special occasion win-back email examples. Time for our Friday Flight. Lifting the Fog of More Around Your Credit Unions Cybersecurity Are you suffering from Cyber FOMO Fear of cyber-threats Overwhelmed by marketing claims Mystified by cyber wizards Out of patience with technobabble.
A satellite return Internet connection is an arrangement in which incoming data arrives at your computer from a satellite downlink and outgoing data such as your request for the next Web page is sent over a regular telephone line. An effective marketing pitch deck should be easy to understand convey trustworthiness and be persuasive enough to elicit FOMO from your audience. With Windows 11 requiring TPM 20 chips just what are the.
Jayathma is a Sri Lankan Dubai-based content creator managing multiple social media channels for both Crypto Sheiks as well as Arts DAO. Satellite return Internet connection. Over the last decade the FBI has continually expanded its Cyber Division.
Explore our cruise itineraries and choose from a variety of rooms depending on your needs and budget. View All Deals Home Windows 11 Windows 11 Guide Best TPM 20 Modules for Windows 11 in 2022. Start planning your next cruise vacation by selecting a destination and departure port.
Torq allows any security professional to connect to any system anywhere and easily create automated workflows that streamline security processes. Cyber Monday Computer Deals. This is undoubtedly a good thing.
The feedback email template. There is a lot of short wordacronyms used in technology and here I attempt to put them together for a reference.
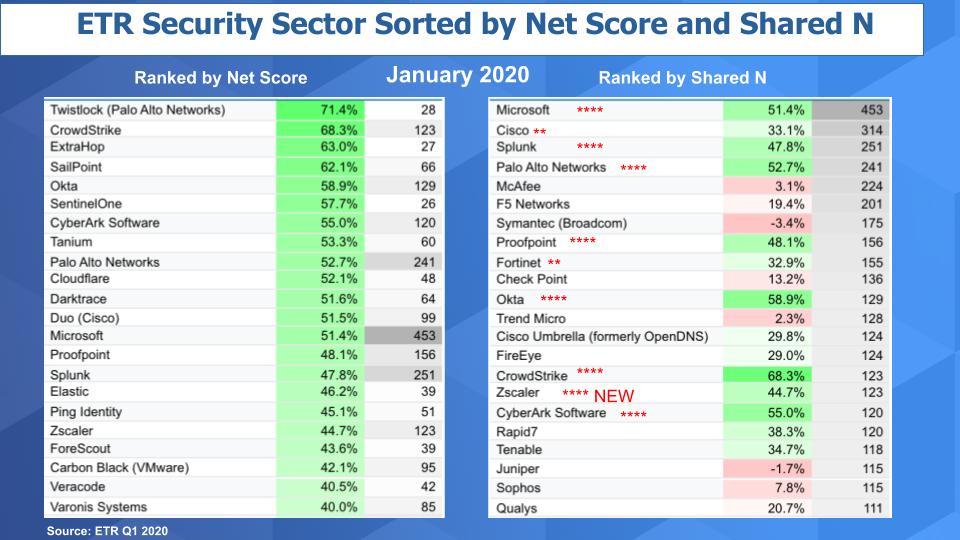
Breaking Analysis Cyber Security Tailwinds In The Post Isolation Economy Wikibon Research

Breaking Analysis Cyber Security Tailwinds In The Post Isolation Economy Wikibon Research

Cyber Security Its Types And Advantages Cyber Security Education Cyber Security Technology Cyber Security Awareness

Cyber Security Basics 5 Types Of Attacks Cyber Security Cyber Security Awareness Cyber Attack

Breaking Analysis Cyber Security Tailwinds In The Post Isolation Economy Wikibon Research

Fomo Why Do We Get Fear Of Missing Out Ionos

Fomo Friday M2 Updates And Cybersecurity Keeping Your Coins Safe Cyber Security Cryptocurrency Tech Company Logos
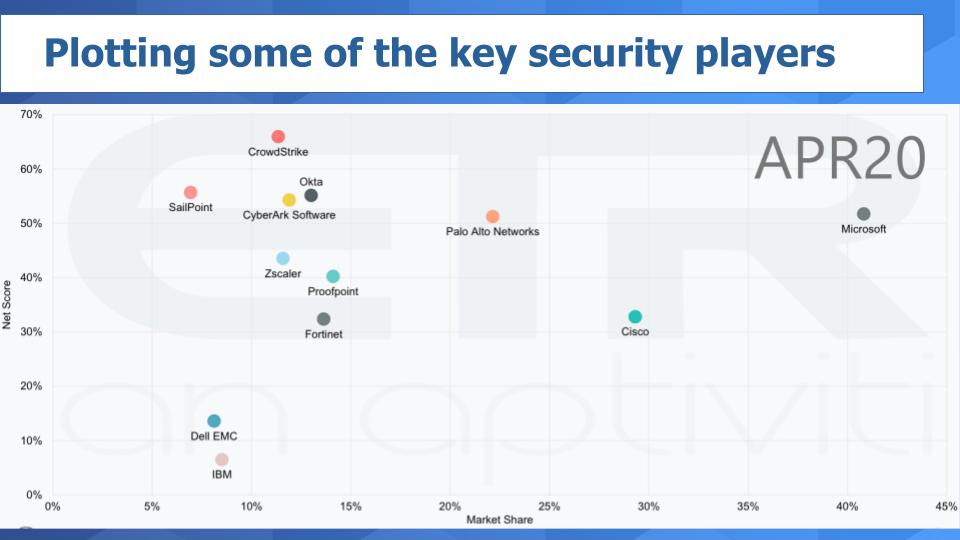
Breaking Analysis Cyber Security Tailwinds In The Post Isolation Economy Wikibon Research
0 comments
Post a Comment